TISAX®, Recertification, ISMS
August 15, 2024
TISAX® labels are generally valid for three years.
The three years are calculated from the end of the assessment process (Closing Meeting on the last audit day), regardless of whether you completed the assessment with or without deviations. Therefore, we always recommend our clients to start the renewal of your TISAX® label at least one year before the deadline. This saves you grace periods and potential difficulties in acquiring new orders that require TISAX®.
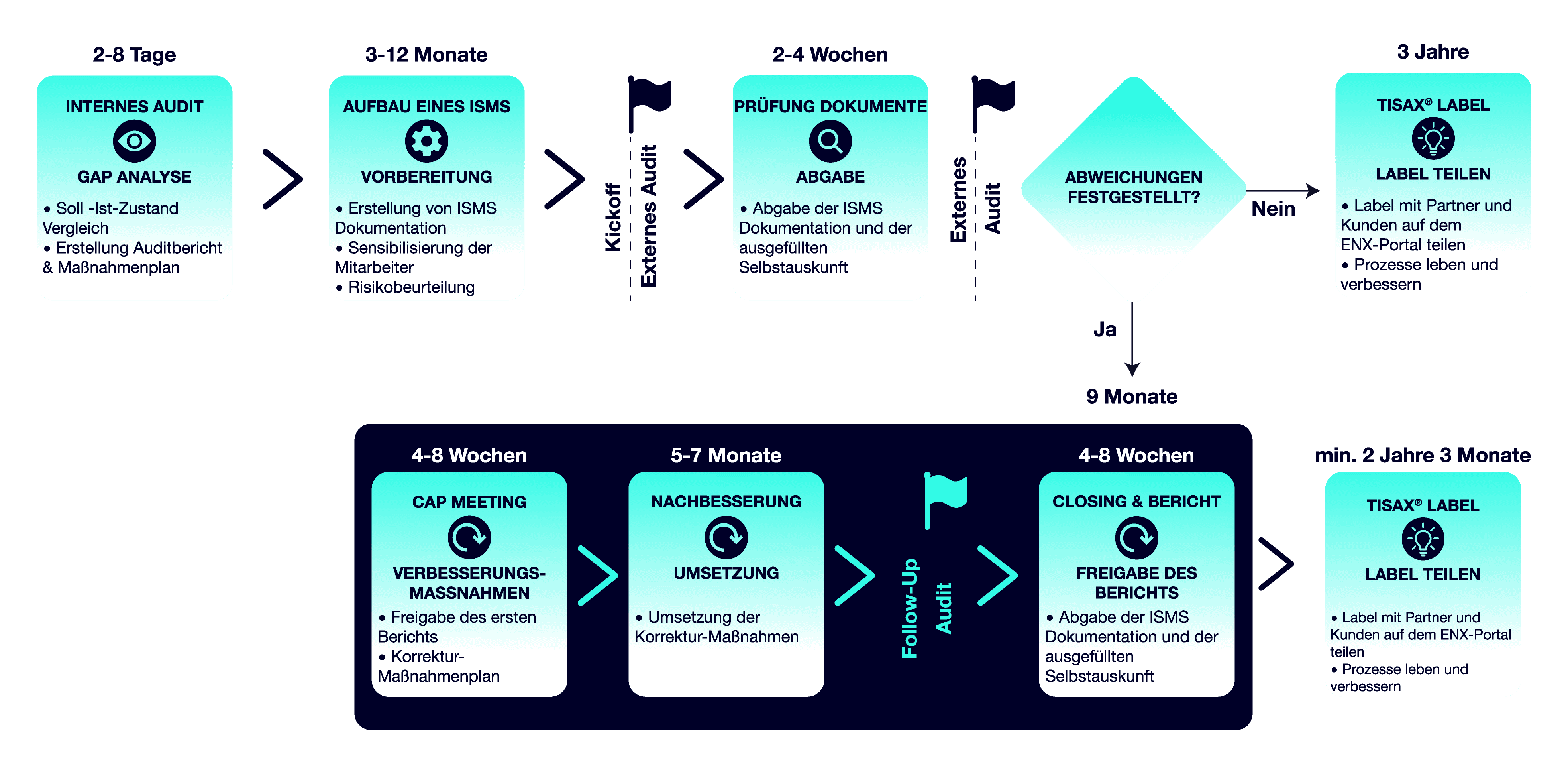
After the three years have expired, the label must be renewed.
For this, the TISAX® process must be conducted again. For this, companies need to register a new scope in the ENX portal, have it re-assessed with the new scope ID by an approved auditing service provider, and share the audit results with partners and clients on the ENX.
As in any management system, a continuous improvement process must be ensured. Therefore, companies that have previously been certified according to TISAX® should create evidence of a continuous and sustainable active use of the defined ISMS processes. To establish this resource-efficiently and cost-effectively, the Deming principle (PDCA cycle) can be applied, for example.
Plan: This is about regularly defining the corporate goals and the information security goals of top management for the coming period, conducting an internal audit, also known as scope & gap analysis, as well as a risk analysis to compare the current and target states. As a result of these analyses or planning phases, actions are defined and transferred into a scheduled action plan.
Do: In this phase, the set goals and defined actions from the planning phase are developed and implemented. Care should be taken to regularly raise employee awareness and communicate the new regulations.
Check: To monitor the effectiveness of the defined processes and continuously improve them, key figures must be collected and limit values defined. For example, the effectiveness of technical and organizational measures and employee awareness can be examined through penetration tests or simulated incidents and phishing campaigns.
Act: Through various reviews and feedback from employees and process owners, it may become necessary to redesign, optimize, or withdraw goals, guidelines, and processes. This optimization phase helps to continuously improve the company’s security strategy and increase the security maturity level.
Do you have questions about the process? Are you facing the recertification process or lacking time and resources to make your ISMS sustainable?



